Spokes v1.3.9
Published at September 25, 2022 · 4 min read
Share on:Spokes v1.3.9 expands our Admin API and adds some new basic features to dashboard and fixes some bugs.
You can find the updates on downloads page, Docker Hub and our RPM repository.
API for Managing Firewall
We’ve extended the existing APIs for creating and updating HTTP sites and TCP applications to include a new property for adding IPv4 and IPv6 filtering. This mechanism has been available for some time, but could only be configured using the client application.
The firewall is an optional property that can be used in the requests for these two endpoints:
firewall is an array of objects that include three fields: sequence, action and network. The sequence field is an integer value that should be greater 0. Sequences are used to order the application of the firewall rules.
The action field can be two values: allow and drop. When traffic is allowed then the firewall mechanism will allow the incoming request to pass through and be routed to the tunnel, and eventual upstream application. When traffic is dropped, the incoming connection will be dropped by Spokes.
The network field uses CIDR notation to determine if the IP address of the incoming request belongs to a network or to an individual host. Some examples of using CIDR notation is the following: 1.2.3.4/16 for IP4 or 2345:0425:2CA1:0000::0000/64 for IPv6. An individual IPv4 host can be identified using the /32 netmask. An example of that is 1.2.3.4/32.
The sequence is treated as optional by the server. It will use the order the objects to determine sequence values.
An important behavior to note of firewall rules is that mixing different allow and drop actions will nullify some of the rules. drop is an exclusive behavior, it will allow all traffic except the hosts or networks specified in rules with this action. allow will filter and drop all traffic except for requests from networks or hosts that are identified in the network portion of those rules.
So if you drop one network and then allow a completely different network, then the drop rule is not effecting any traffic.
Additional details and notes on using Firewall rules are available in our updated API docs.
Firewall Rules in Dashboard
We’ve added the ability to view the firewall rules for TCP applications and HTTP sites using the dashboard.
Visit a tunnel details page that will list the HTTP, TCP, and other specific details. Select any of the traffic rules to inspects its details, including any firewall rules now.
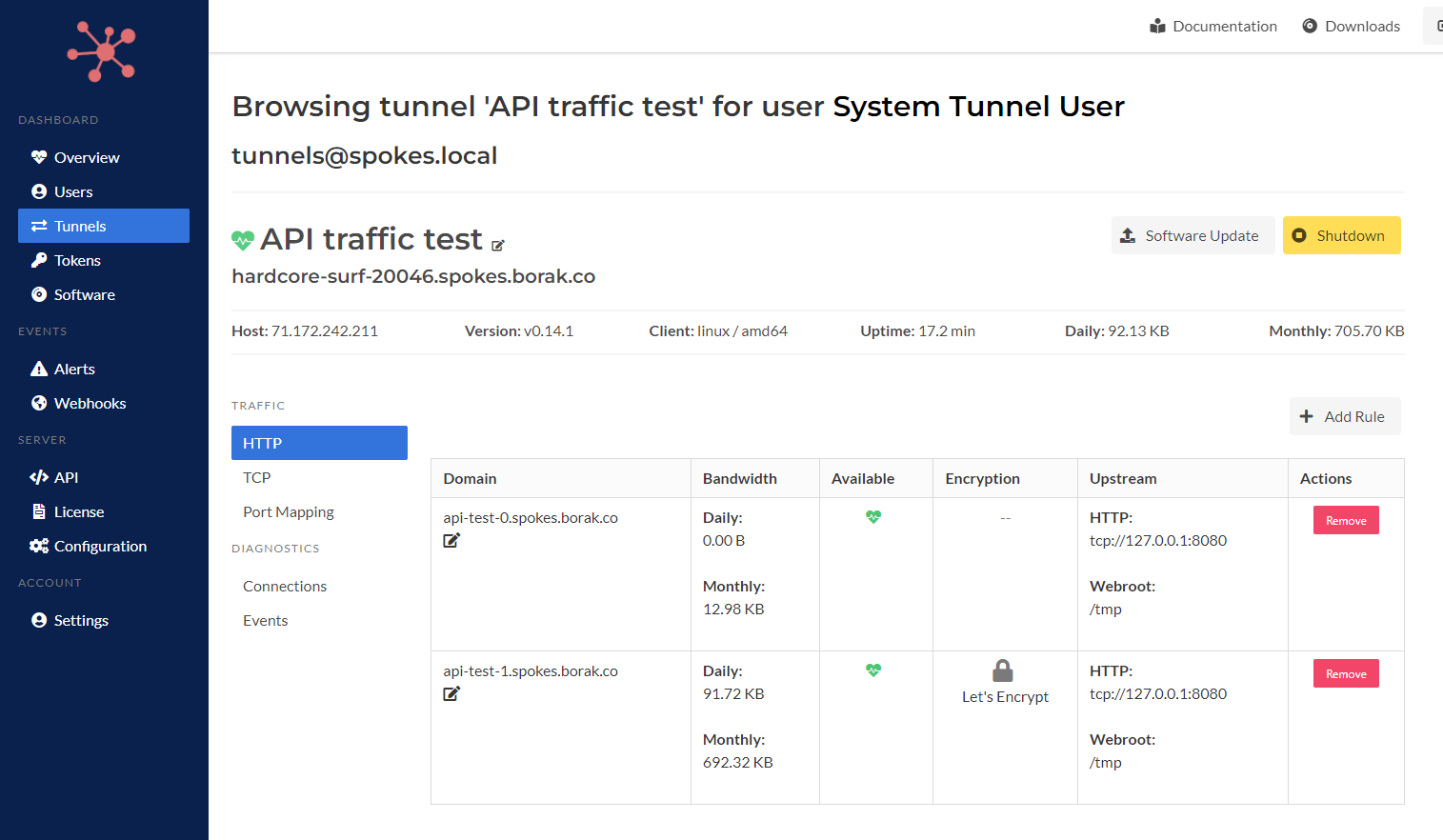
Tunnel Details Page
In the screen capture below you can see the firewall rules setup for this specific HTTP site. A specific IPv4 and IPv6 host is identified using CIDR notation.
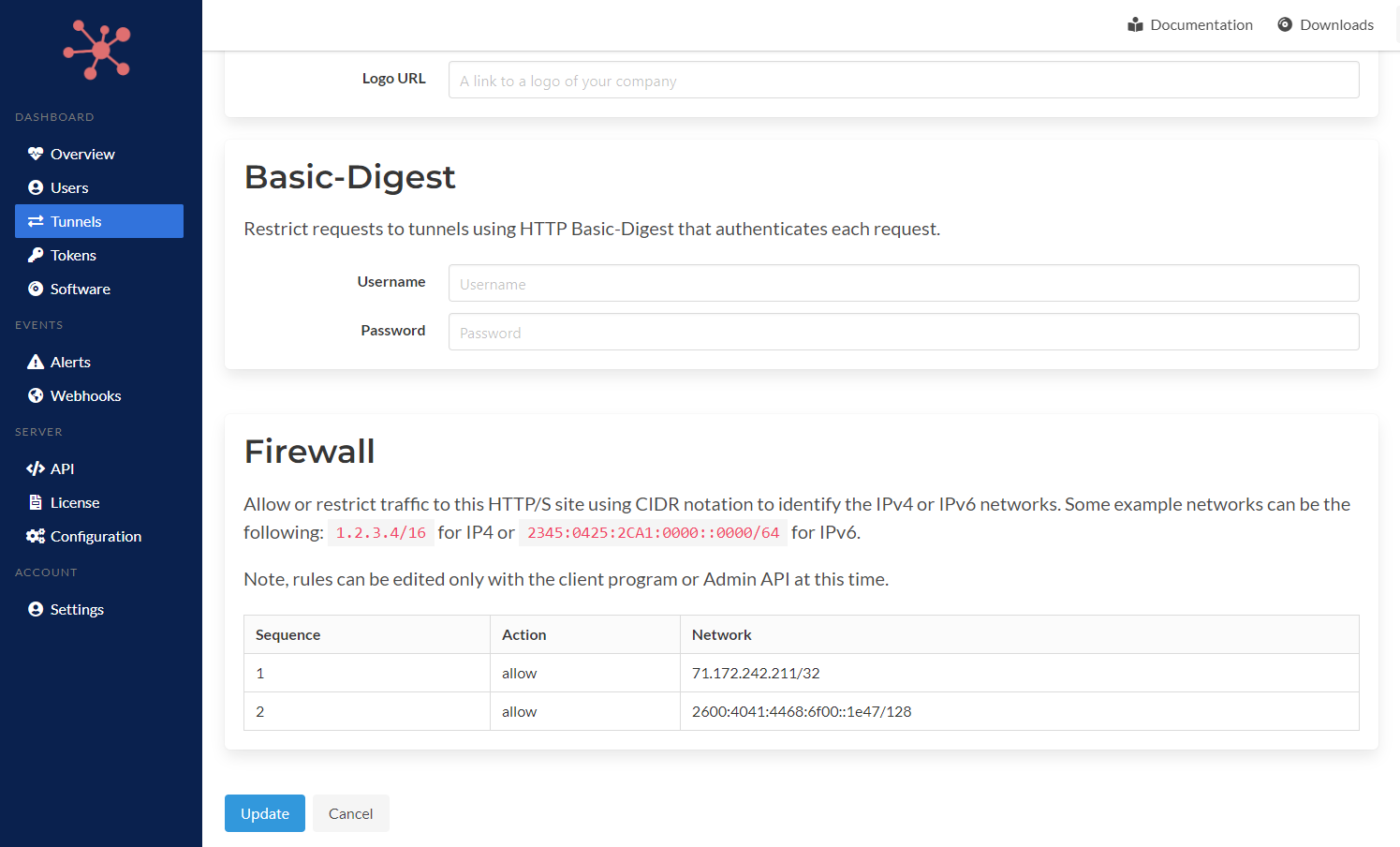
Firewall Rules
At this time firewall rules can only be viewed in the traffic rules page. In the future will add new functions to edit and manage them from the dashboard UI as well.
Removing Stale Client Releases
Spokes can synchronize releases of the pktriot client program so that it can be used to archive and stream updates to online tunnels. These releases can grow over time and accumulate space on your server so we’ve added a small button next to each release so that you prune older versions over time.
Bug Fixes
As we were adding new support for managing Firewall rules with the API we discovered some previous state of firewall rules that were not being cleared when tunnel sessions are terminated or closed. This cause issues when those rules were updated.
What’s Next?
We’ve been designing a new clustering feature for Spokes that will make high-availability a snap to implement. This feature will be used to introduce others such as load balancing across multiple tunnels. We’re hoping that this will be out next big release, v1.4.0, and we’re working to have it available in November.
Let us know if we can focus on any other new features or improvements, cheers!