Spokes v1.1.2
Published at April 11, 2021 · 3 min read
Share on:Release v1.1.2 builds on-top of the unannounced v1.1.1 release with making container-based installation and deployments simple to set up and configure. Previously we only supported RPM packages for Linux, however, containers allow us to support more Linux distributions and container orchestration platforms like Kubernetes.
We are also supporting a Homebrew package for macOS. Installs and upgrades using the brew package manager are now possible. An example command is below:
[user@macos ] brew install packetriot/homebrew-tools/spokes
More details on our container deployment update and other new features below.
Our documentation has been updated for container installations and the next steps after first-running it.
Container Installation
v1.1.1 introduced initial support for a container image and deployment. However, it wasn’t seamless and required stepping in and out of a shell to configure the Spokes container instance.
Release v1.1.2 adds two new environment variables that will be used to initially auto-configure the Spokes server using a self-signed certificate. The DOMAIN variable is used to set the domain name for the Spokes server, e.g. spokes.example.com. This value is accepted as is and we do not check the network (DNS) to ensure it is valid.
You then visit the a URL https://spokes.example.com in a browser to finish setting up Spokes through the admin dashboard.
The ADMIN_SECRET variable is used to set a temporary secret that can be used to authenticate a visitor so that an admin user can be created.
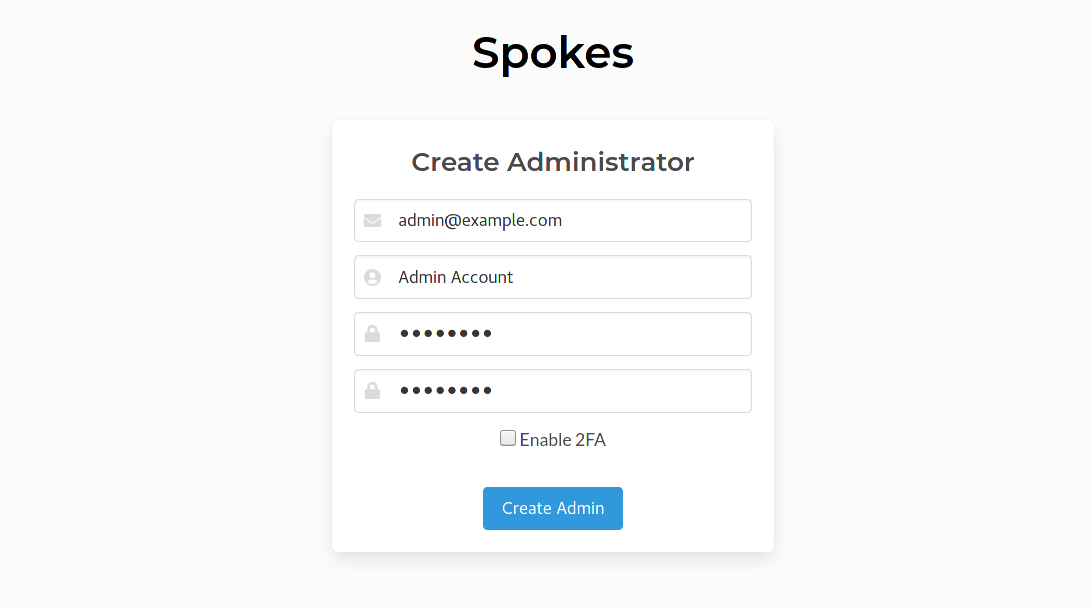
Create Admin User
Once an admin is created they can log into Spokes and then change the domain and the TLS settings to use custom certificates or Let’s Encrypt. More information on the container setup is available in docs here.
Server Configuration
In the server configuration page the domain name that is used to access the Spokes server can be updated. This new value is validated to ensure that the server will be accessible with the new domain name. If DNS is not properly set an error will be flagged to the user.
TLS options can be changed as well. Admins can enable Let’s Encrypt for creating and maintaining TLS certificates through the dashboard. Custom certificates can be loaded as well.
Validation checks are performed to ensure that the domain name can be verified with the custom certificates uploaded. The HTTPS server is restarted dynamically and will reload with the changed settings.
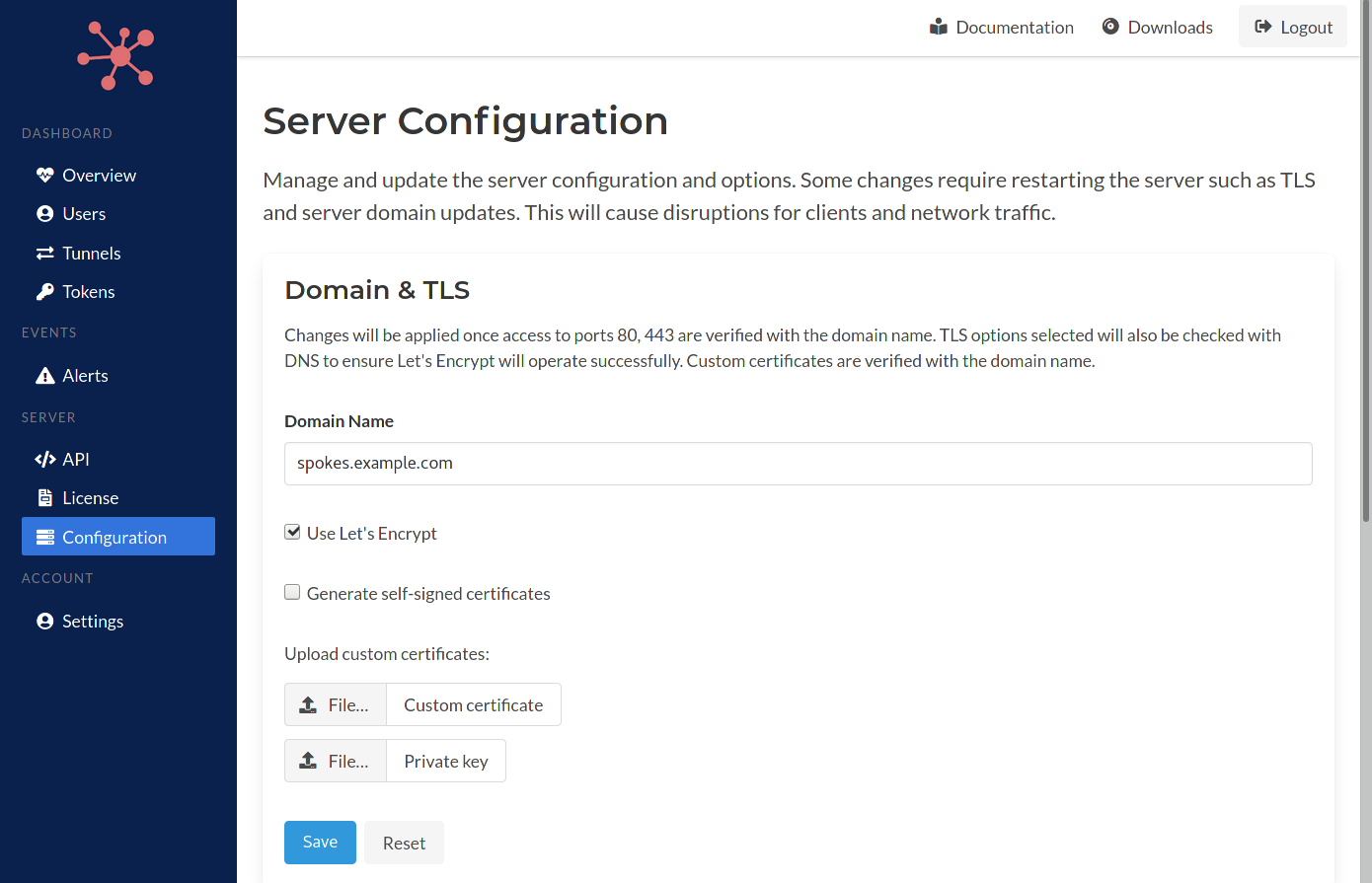
Domain & TLS Server Settings
More screenshots and information is available in our docs.
In addition to the domain and TLS options, settings for the tunnels can updated and modified here too. These options include the maximum number of ports a tunnel can allocate and use and the number of data connections a tunnel can use for relaying traffic between the Spokes server and it.
We’ll be adding more options to this page over time to make configuring Spokes a breeze and not require open a shell or restarting the process.
Coming soon!
We are working on Webhooks for publishing events to external systems. Events such as tunnel creation and deletion, tunnels coming online or offline, admin logins and more. With webhooks, developers will be able to interact with services behind tunnel and do so without constant polling of the API to learn the state of tunnels.
Thanks again to our users and customers who have shared their feedback and suggestions to us.
Cheers!