Spokes v1.5.4
Published at September 8, 2025 · 5 min read
Share on:We’re excited to announce the release of Spokes v1.5.4, bringing several powerful new features and important bug fixes to enhance your experience with the Spokes Gateway server.
Get the Release!
You can download the RPM here. As always, our container images are available in both the Packetriot and Terrapin Labs repositories.
docker pull packetriot/spokes:1.5.4
# alternatively
docker pull terrapinlabs/spokes:1.5.4
Registration Tokens
In this release, registration tokens have been updated to support more granular limits. You can now configure.
- Expiration dates, which provide tokens with a limited lifespan, automatically expire if they are lost or forgotten.
- The maximum number of tunnels that can be created with a specific token.
- The maximum number of active tunnels that can be instantiated and connected to the Spokes server.
These controls can be used independently or combined to suit different use cases. For example, you can create a token with a high tunnel creation limit but restrict the number of active tunnels at any time. This flexibility allows for more secure and manageable token usage.
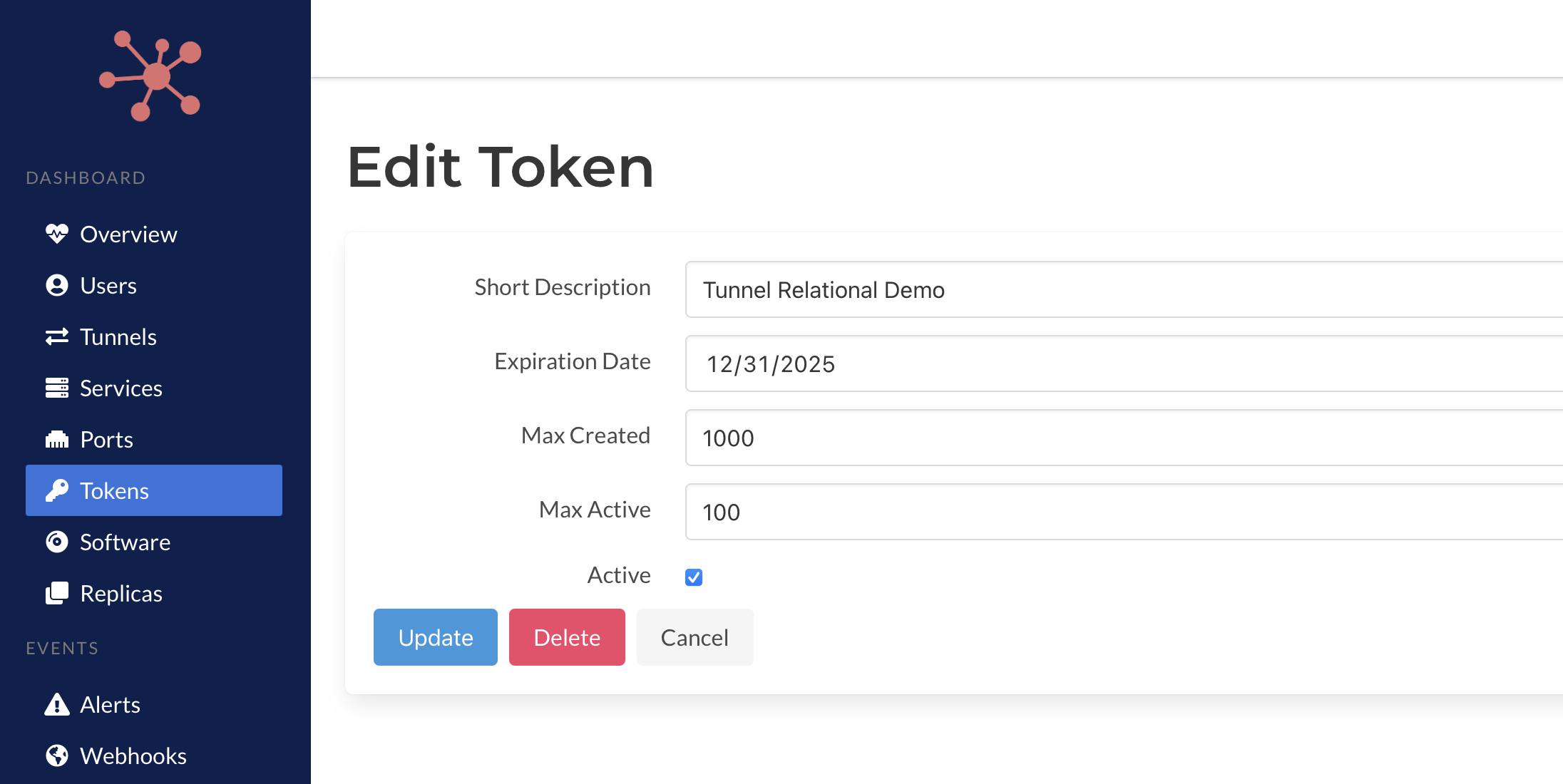
New Registration Token Limits
The table has been updated to show all of the new criteria added to registration tokens. Still, there is a column that highlights the number of tunnels created with a token that has a link to a page to view and browse specific tunnels.
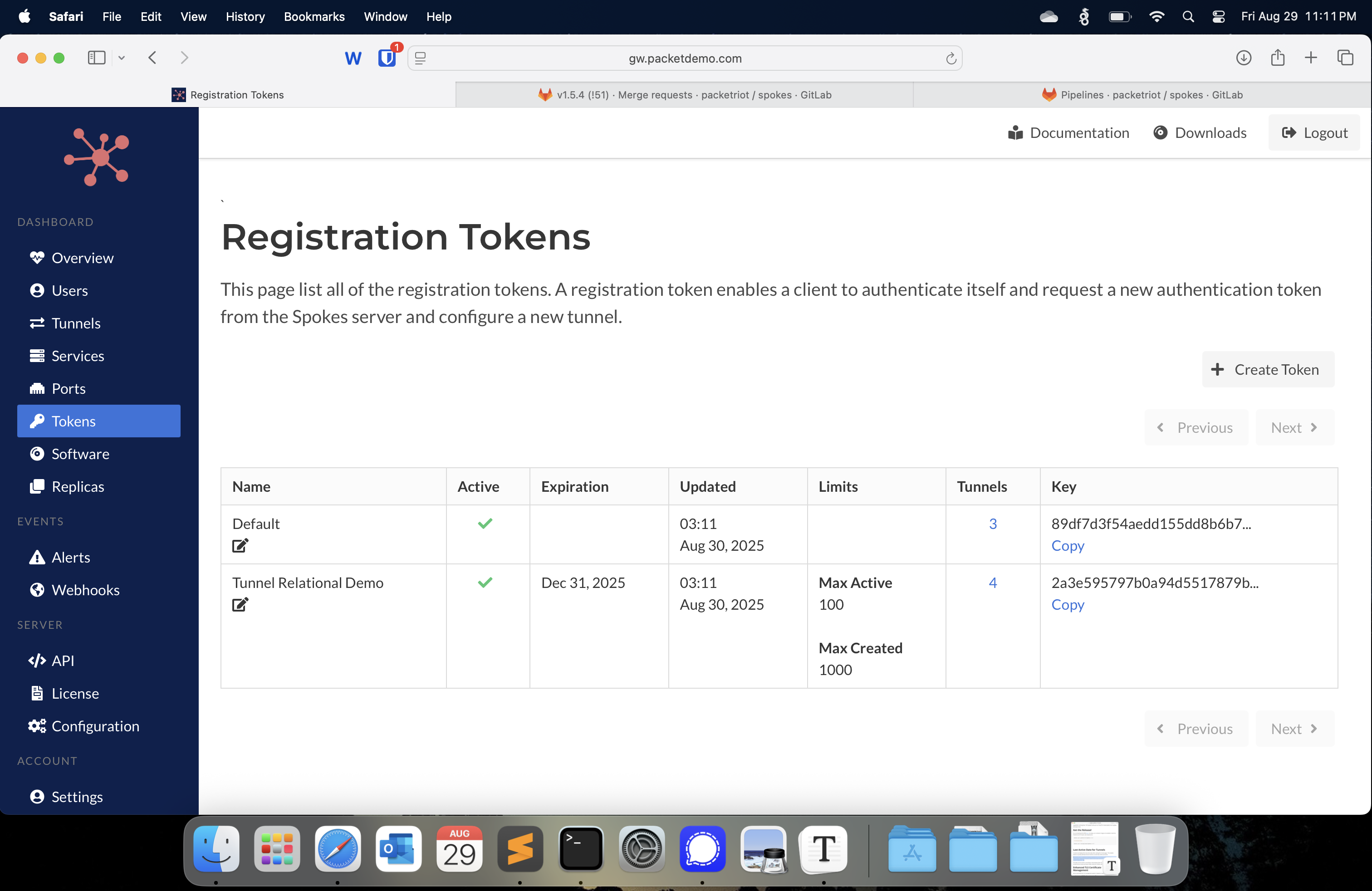
Updated Registration Tokens List
The relationship between registration tokens and the tunnels created using them is now visible with a new page that is available in this release.
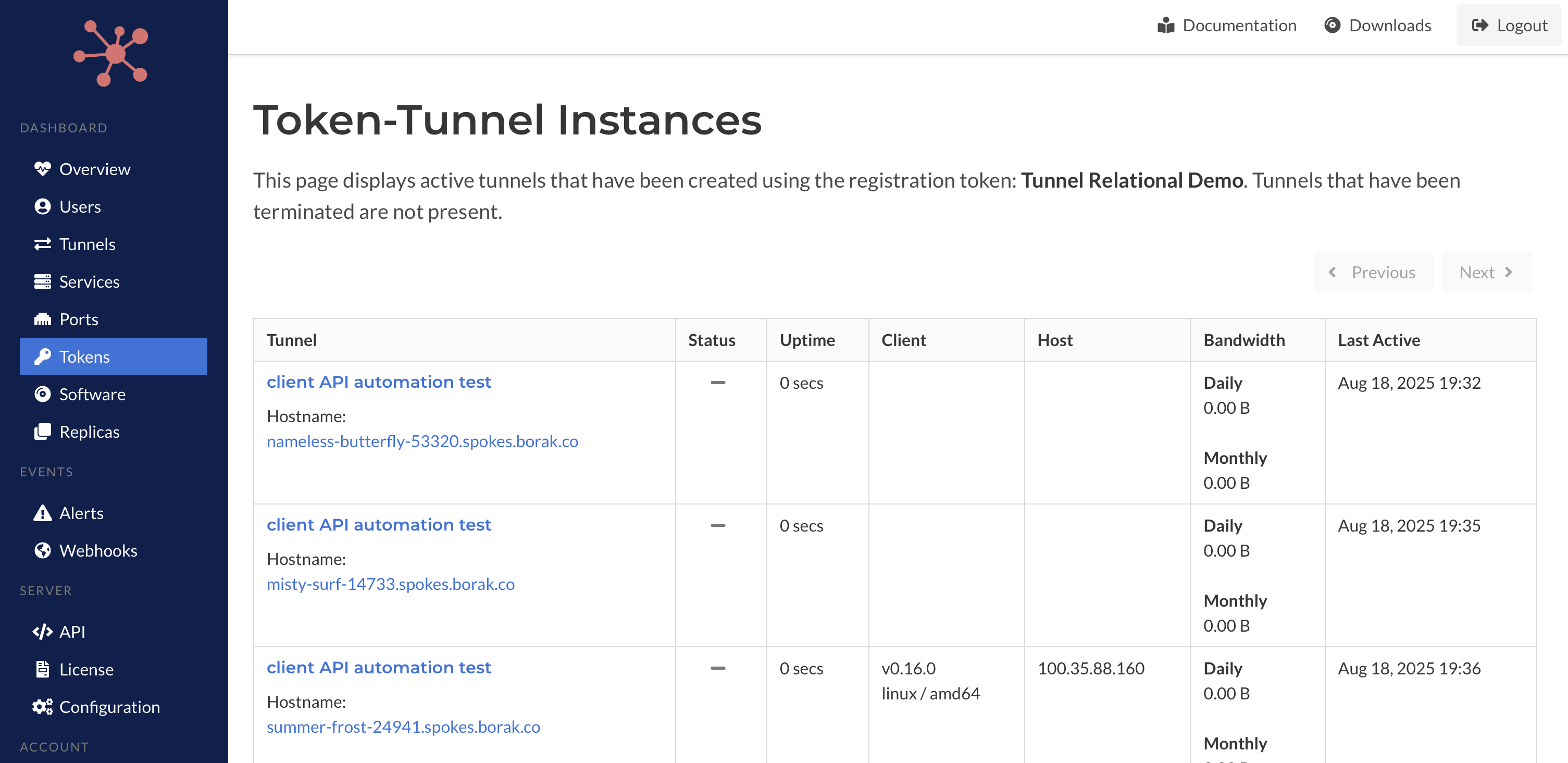
Registration Token to Tunnel List View
Previously created tunnels will not be displayed here since we did not record the relationship. However, new tunnels will begin to show up.
Reverse Proxy
We’ve added a built-in reverse proxy, and now you can create HTTP and TCP traffic rules to proxy traffic to an upstream application running adjacent to the Spokes server. Spokes now behaves like any typical reverse proxy server, such as Apache or nginx, but it supports features not available out of the box, such as:
- TLS management with Let’s Encrypt integration.
- Password portals, including support for OpenID Connect authentication.
- IP Filtering
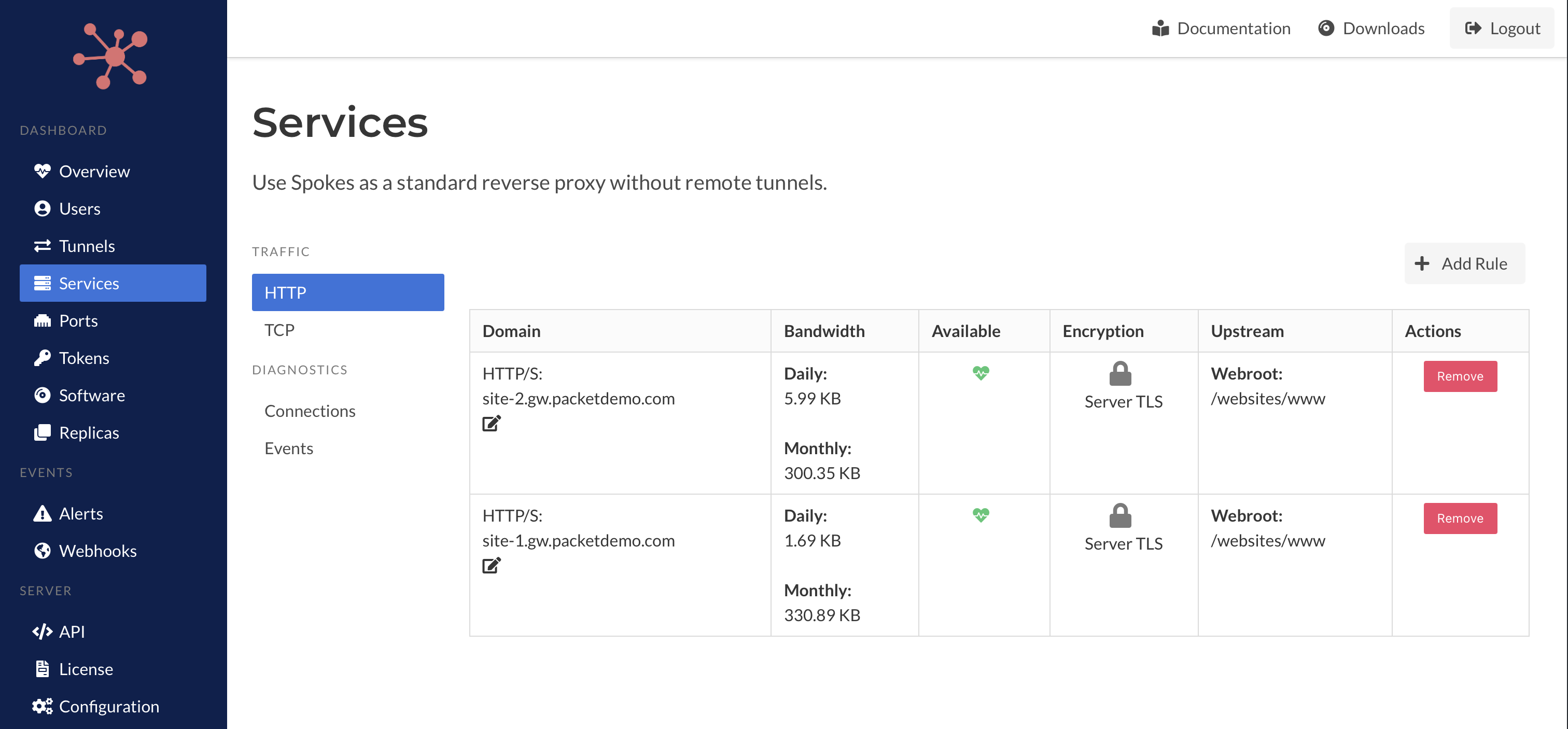
Reverse Proxy Services
This new feature makes Spokes a well-rounded network server, beyond the advanced remote tunneling that is its primary focus.
Spokes basic TCP port forwarding as well in this reverse proxy. This means that if you want to expose local backend services like a Postgres database or Redis server. You can use custom or randomized ports to allocate a public port and forward the traffic as you would typically do with a remotely deployed tunnel.
HTTP - Secure By Default
We’ve made a change in the Spokes dashboard UI and backend such that all HTTP traffic rules created or updated in the Spokes dashboard will enable the secure setting. That means that HTTPS traffic rules will always be requested for any HTTP traffic rule, regardless of the TLS option you choose (or ignore).
Earlier, you could make selections that would only request HTTP traffic and not HTTPS. This change makes sense to us and simplifies which inputs are necessary when creating new rules for HTTP traffic.
We are introducing a new term called Server TLS, which implies TLS session management and termination at the Spokes server’s edge. When this occurs, relaying HTTP traffic to tunnels includes an X-Forwarded-Proto field set to https.
Spokes uses a directory called certs-extra, located in /var/lib/spokes/certs-extra, where TLS certificates can be organized into subdirectories. This feature was added a long time ago, but is not thoroughly documented.
The Packetriot network uses this feature to store wildcard TLS certificates that are used to terminate TLS connections for *.pktriot.net and other Packetriot domains. But it can also be used for private Spokes servers and can alleviate throttling by Let’s Encrypt, if it’s used widely by a customer.
This mechanism for TLS termination and session management will now be referred to as Server TLS moving forward, and is a new-ish TLS option for HTTP traffic rules.
UI Enhancements
We streamlined the user interface for creating and updating HTTP traffic rules for remote tunnels and our reverse proxy. Earlier, we provided input fields for all the possible values one could input, mirroring the pktriot CLI.
In this release, we refactored the UI so that you can choose an upstream method and then only see the relevant fields. For example, if you want to use an upstream URL, you would only be presented with that field, along with the appropriate optional fields, such as Insecure Upstream TLS.
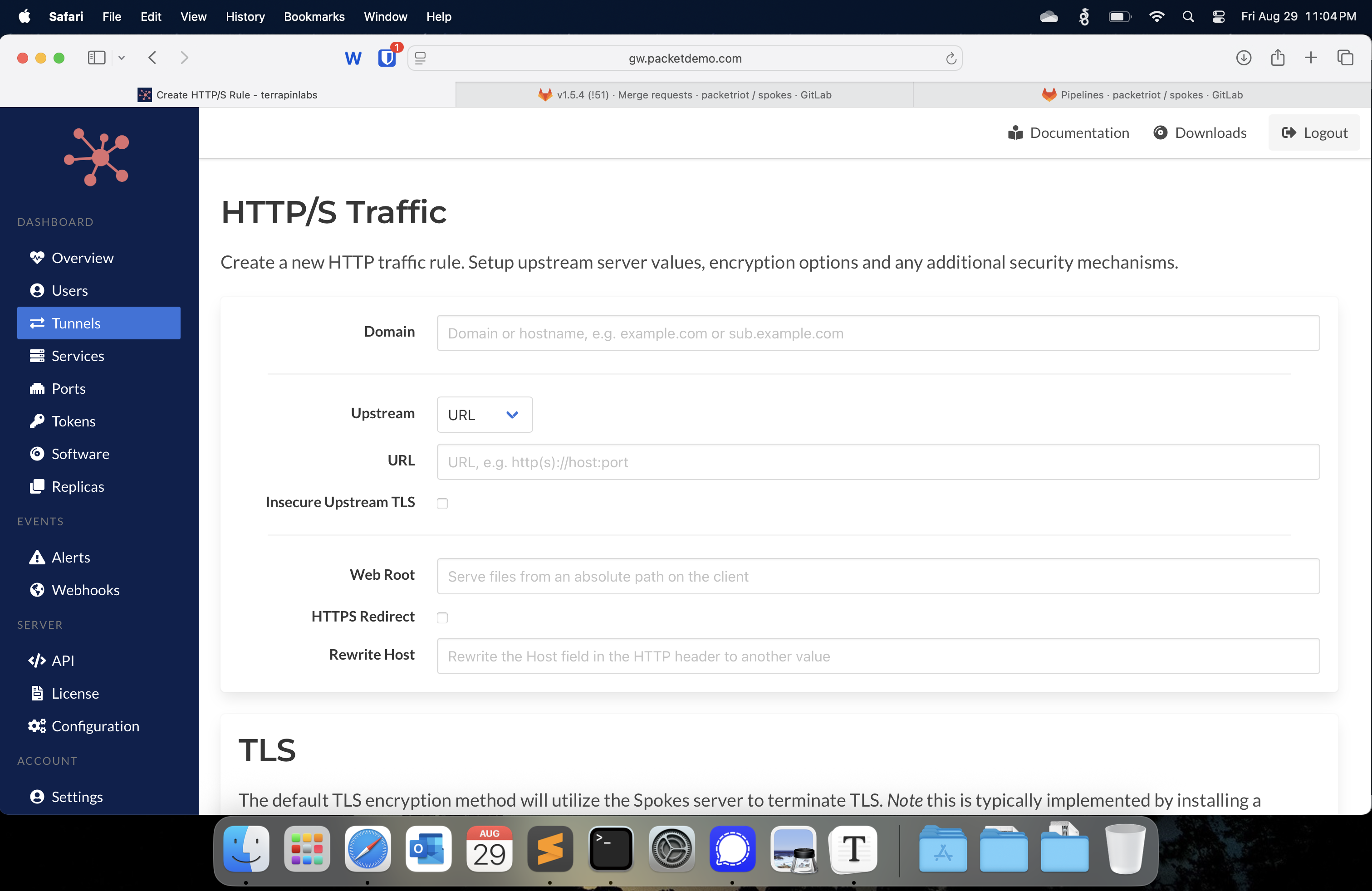
Upstream URL Inputs
When you select the manual method, you will receive just those relevant input fields: destination, HTTP port, and optional TLS port, which is used for transparent TLS proxying.
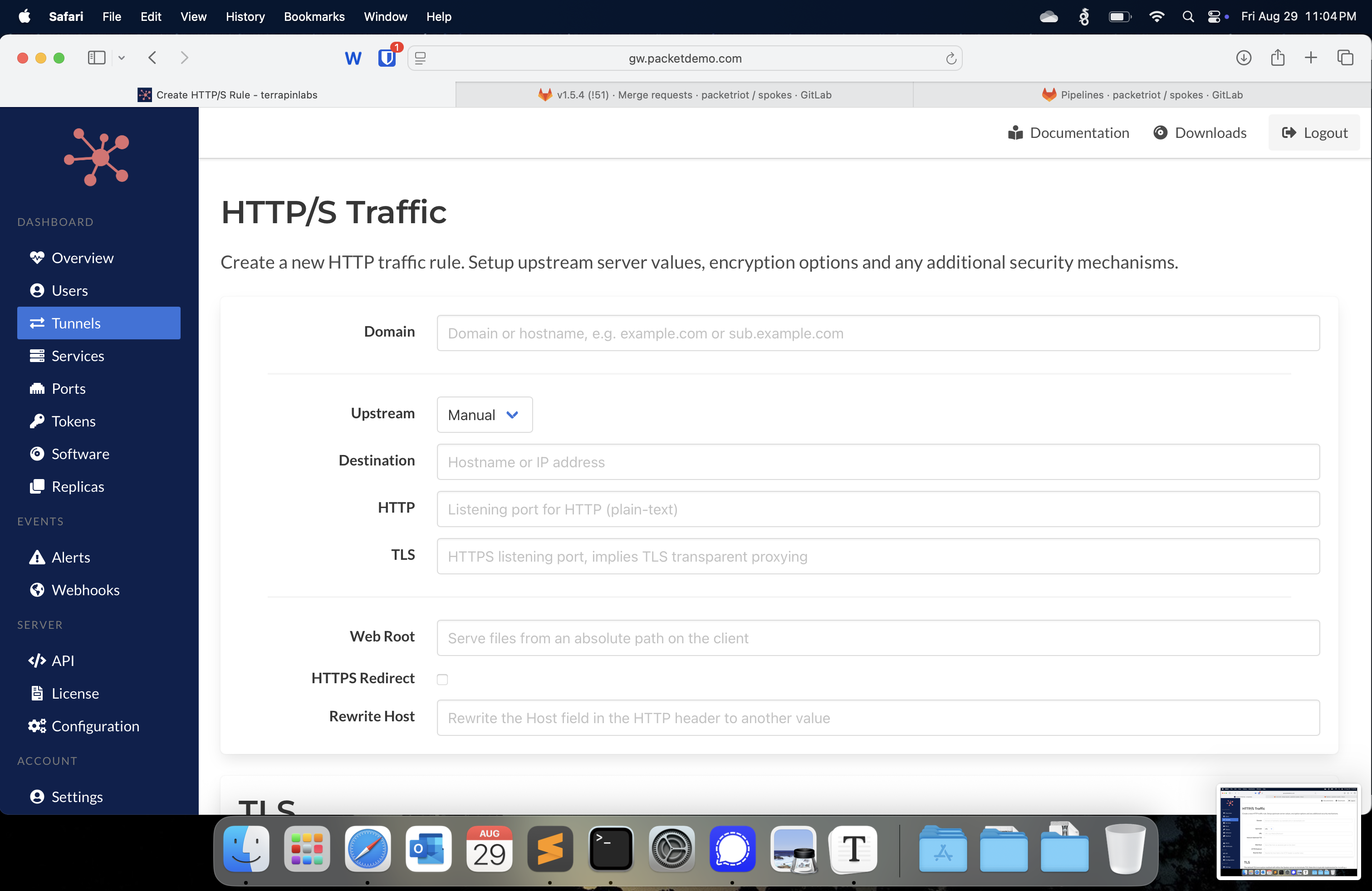
Manual Upstream Inputs
These changes should reduce errors and confusion on which input fields to use and when. In addition to these changes, we similarly streamlined TLS settings for HTTP traffic rules. We added a combo box that will dynamically present custom certificate file upload inputs when selected. The combo box includes a setting for Let’s Encrypt or Server TLS.
Certificate Management Fixes
We fixed several bugs, including improved prioritization for static TLS certificates. Spokes now correctly prioritizes static certificates above ACME-based certificates (such as those issued by Let’s Encrypt or ZeroSSL), ensuring your custom TLS setups are properly respected.
If you are using static TLS certificates in your deployments, we strongly recommend upgrading to v1.5.4 to benefit from the fixed prioritization behavior.
Improvements & Bug Fixes
We added security headers to our HTTP and API responses to improve the security of Spokes: X-Frame-Options, Content-Security-Policy, and X-Content-Type-Options.
Roadmap
In our next release, we plan on adding a new page to the dashboard to manage TLS certificates in the certs-extra directory. We will explore expanding the API as well to do it programmatically and also via the CLI.
Thanks!
As always, we want to thank our users for their valuable feedback and bug reports. Your input drives continuous improvements to Spokes. If you have ideas for features or enhancements, please don’t hesitate to reach out.
Cheers!