Spokes v1.5.5
Published at October 15, 2025 · 3 min read
Share on:We’re excited to announce the release of Spokes v1.5.5, bringing new features, bug fixes, and minor improvements to enhance your experience with the Spokes Gateway server.
Get the Release!
You can download the RPM here. As always, our container images are available in both the Packetriot and Terrapin Labs repositories.
docker pull packetriot/spokes:1.5.5
# alternatively
docker pull terrapinlabs/spokes:1.5.5
TLS Management
In our last update, v1.5.4, we mentioned that we would be adding support for viewing and modifying the certificates that are used to establish TLS sessions at the Spokes servers’ edge. This feature is used in Packetriot to support TLS termination for the thousands of tunnels hosted across our network, utilizing domains such as pktriot.net, reversetunnel.net, betabuild.dev, and others.
Many users who host Spokes on their own and serve hundreds of tunnels have used Let’s Encrypt on the tunnel side to generate TLS certificates and terminate TLS sessions there. This works, but it bumps up against the rate limits for Let’s Encrypt and isn’t scalable.
The new TLS page in the server settings section of Spokes allows you to upload, view, and manage TLS certificates and keys that are used to terminate TLS sessions at the Spokes servers’ edge and help you scale to bringing up thousands of tunnels quickly and securely.
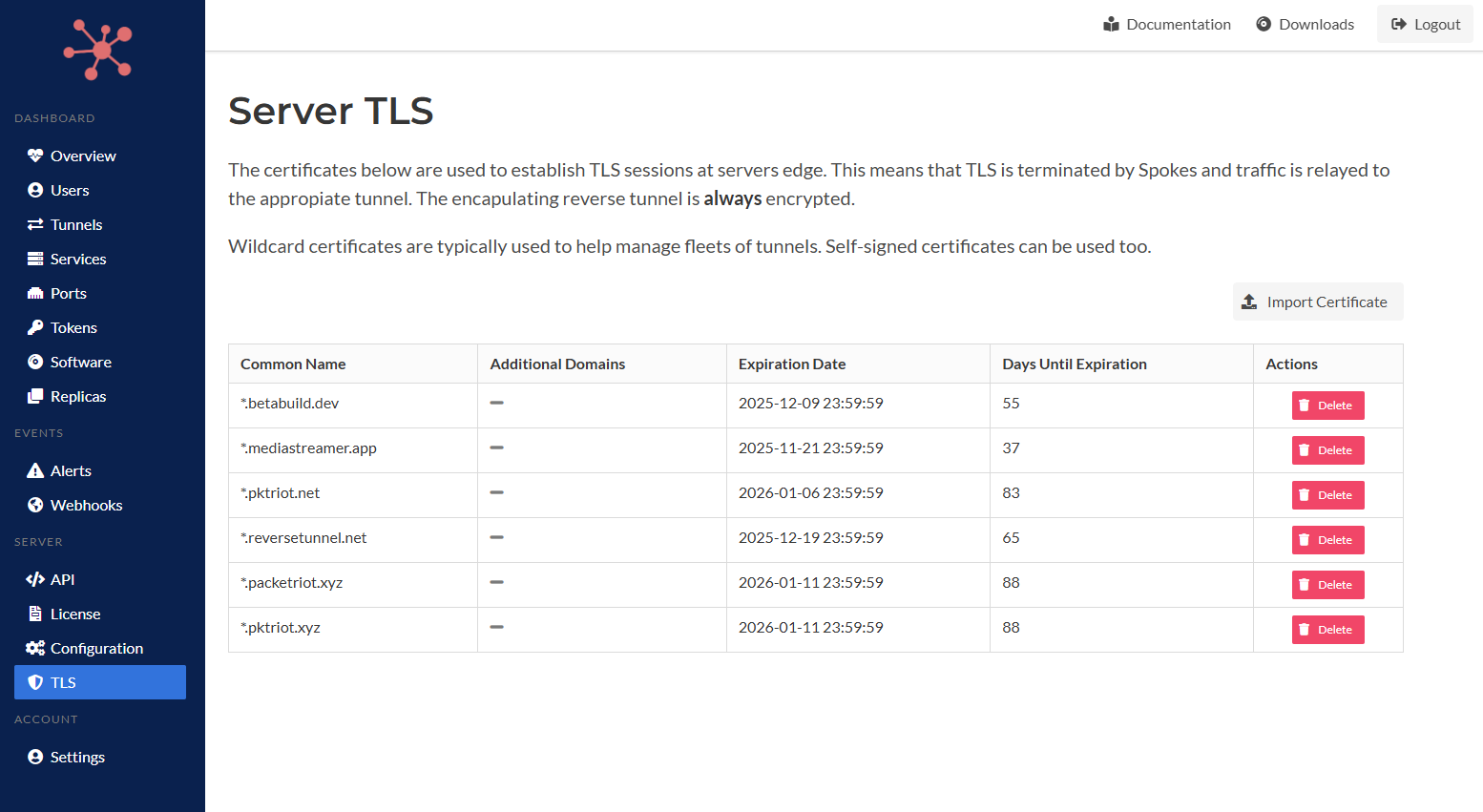
Server TLS Management
This feature has been in Spokes for quite some time, but has been buried in configurations and conventions on our instances we host to operate the Packetriot network.
In our last release of Spokes, v1.5.4, and the Packetriot client v0.16.0, we enabled HTTPS traffic always and now default to Server TLS when no TLS options are specified. This mode will expect Spokes to terminate the traffic. This makes it simple to enable TLS traffic for thousands of tunnels and avoid deploying sensitive TLS certificates and keys.
Web Application Firewall
There is an emerging web application firewall (WAF) that we are creating inside Spokes. It is currently being used for specific use cases in hosting the Packetriot network, but I think it will grow into a generally useful feature.
Similar to the Server TLS management feature that was hidden for years in Spokes behind deployment conventions and integrations, the WAF may eventually become a feature exposed to all Spokes users, helping to introduce more security mechanisms for upstream applications.
If this sounds useful to you or you have use cases in mind, please reach out to us. We’d like to understand how this feature could be helpful.
Thanks!
As always, we want to thank our users for their valuable feedback and bug reports. Your input drives continuous improvements to Spokes. If you have ideas for features or enhancements, please don’t hesitate to reach out.
Cheers!